Table of Contents
Introduction
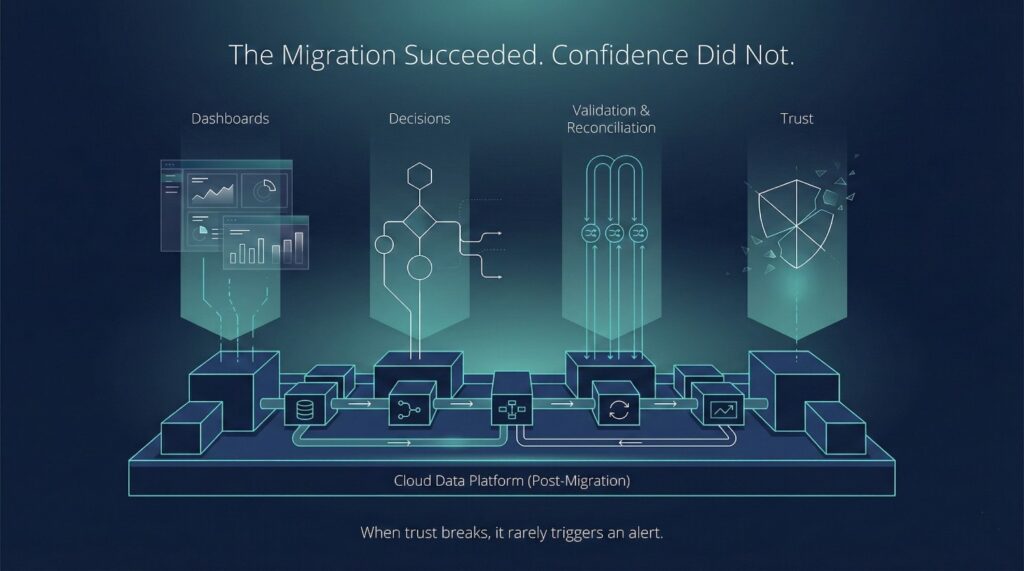
Many cloud data migrations are declared technically successful.
Pipelines run.
Data loads complete.
Dashboards refresh on schedule.
From an engineering perspective, the project checks all the boxes.
And yet—quietly, without escalation—business teams stop using the data.
They export to spreadsheets.
They ask for manual reports.
They double-check numbers they used to trust.
By the time leadership notices, confidence has already eroded.
What makes this failure particularly dangerous is that it rarely appears on project dashboards. Migration status reports track jobs completed, data volumes moved, and costs reduced—but they do not track whether decisions are actually being made from the new system. By the time adoption metrics surface the problem, trust has already shifted elsewhere.
The Trust Failure No One Tracks
In practice, this failure often shows up first as a behavioral signal, not a technical one: fewer executive questions answered directly from dashboards, more follow-up emails asking for confirmations, and a growing reliance on “offline” numbers for high-stakes decisions. These signals are easy to miss because they don’t register as incidents—but they are early indicators of erosion.
This is one of the most expensive kinds of migration failure because it is invisible at first.
There is no outage.
No rollback.
No postmortem.
Instead, the failure surfaces as a gradual behavioral shift:
- Fewer decisions made from dashboards
- More “just to be safe” reconciliations
- More questions about where numbers come from
- Less reliance on the new platform as a source of truth
The system functions—but confidence in the system erodes.
Why Trust Is Harder to Migrate Than Data
Performance is measurable.
Availability is testable.
Cost is trackable.
Trust is not directly measurable in the same way.
Trust depends on:
- Consistency over time, not one successful release
- Clarity of meaning, not just correctness of values
- Confidence that numbers will not change unexpectedly
- A sense that “this won’t embarrass me in a meeting”
Cloud data migration often improves the technical qualities of data while unintentionally destabilizing the social ones.
And once trust is lost, it is often harder to recover than a failed job or a broken pipeline.
What This Article Explores
Industry data shows more than 80% of data migration projects run over time and/or over budget, with cost overruns averaging 30% and time overruns averaging 41%.This article focuses on the side of cloud data migration that most postmortems miss:
- Where trust actually breaks
Not in outages, but in small inconsistencies and unclear definitions. - Why business teams disengage
Even when the platform is faster, cheaper, and more scalable. - How migrations unintentionally undermine confidence
Through validation noise, shifting metrics, and invisible decision-making.
If cloud data migration is treated purely as an engineering success, trust loss is often misdiagnosed as a user error or resistance to change.
In reality, it is often the predictable outcome of how migrations are structured, communicated, and governed. What is often labeled as ‘resistance to change’ is more accurately a rational response to perceived risk in decision-making.
Trust Was Fragile Long Before the Migration
One of the most uncomfortable truths about cloud data migration is this:
Many business teams did not fully trust the data even before the migration began.
The migration did not break trust from a position of strength. It exposed how thin that trust already was.In many organizations, data trust before migration is conditional rather than absolute. Teams trust numbers only within narrow, familiar contexts—specific reports, known filters, or habitual adjustment steps. The migration removes those conditions, revealing that trust was never generalized in the first place.
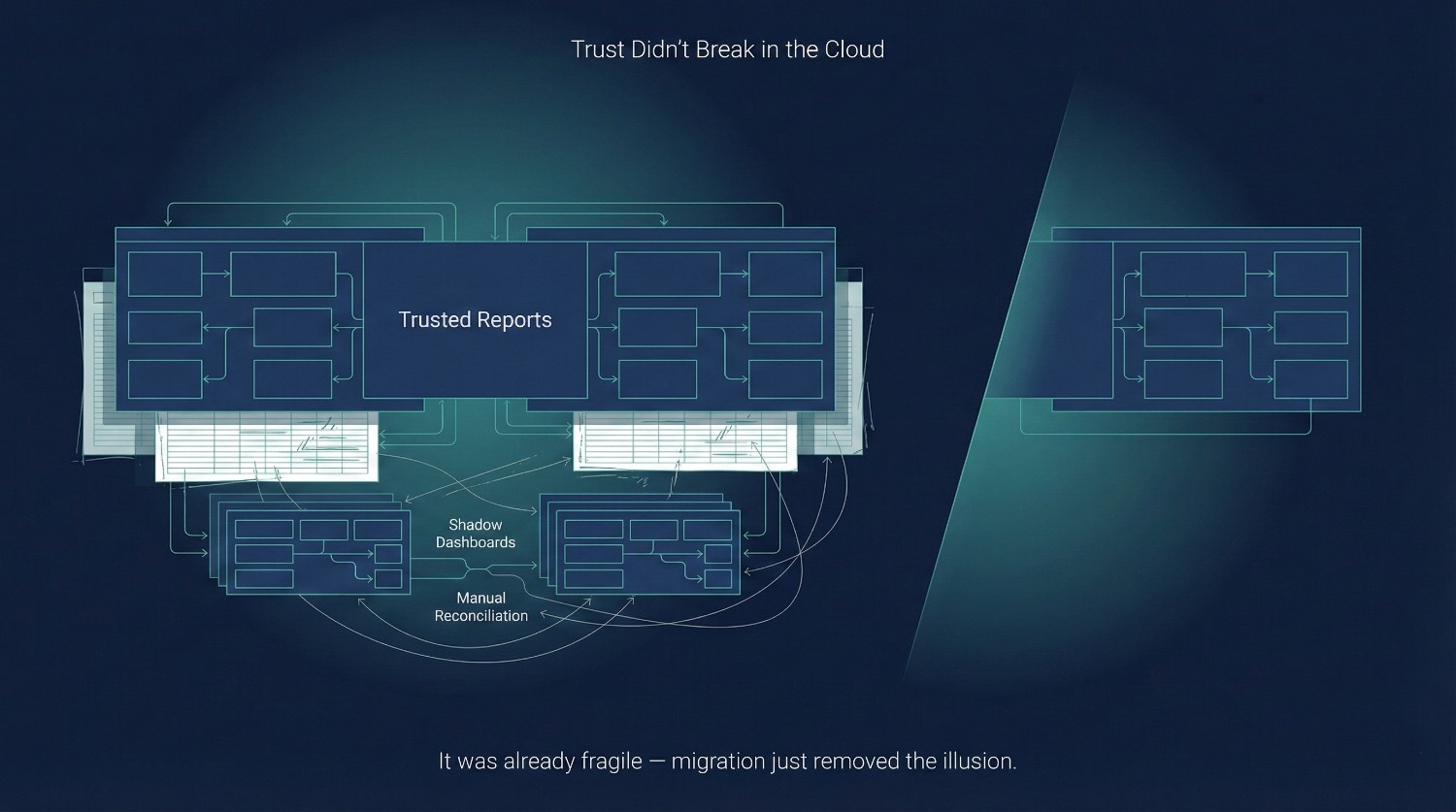
The Legacy Trust Illusion
In many organizations, what appears as trust is actually familiar tolerance.
Business teams learned how to work around known issues rather than relying on the system as-is. Over time, these coping mechanisms became normalized—and were mistaken for confidence.
Common workarounds included:
- Spreadsheets as “final truth”
Data was exported and manually adjusted because it was faster than questioning upstream logic. - Shadow dashboards
Teams built their own reports with slightly different filters to “get the number that makes sense.” - Manual reconciliations
Numbers were trusted only after someone cross-checked them against another system or last month’s file.
These behaviors signal something important: the business was already compensating for weak trust.
Legacy systems often survived not because they were reliable, but because users knew their flaws and learned how to navigate around them.
That familiarity created a fragile sense of safety.
Migration Removes Ambiguity—and Comfort
Cloud data migration disrupts this fragile equilibrium.
Legacy environments allow ambiguity:
- Definitions can be interpreted loosely
- Inconsistencies can be explained away
- Exceptions can be handled quietly
Modern cloud platforms tend to do the opposite.They force greater precision:
- Definitions must be explicit
- Logic must be centralized
- Discrepancies become visible immediately
- Numbers are reused across teams, not customized locally
This precision is technically beneficial—but psychologically destabilizing.
What business teams experience is not “better data,” but loss of flexibility:
- Numbers change without informal adjustment
- Long-standing assumptions are challenged
- Metrics no longer behave the way people expect
Even when the new data is more correct, it feels less safe—because the old comfort mechanisms no longer exist.
This is why correctness alone does not feel like an upgrade. For business teams, safety comes from predictability and interpretability, not from mathematical rigor. When rigor arrives without narrative, it feels hostile rather than helpful.
Trust did not break primarily because the cloud platform itself failed.
It broke because the migration removed ambiguity that business teams had been using as a buffer.
Understanding this is critical. If teams assume trust was strong before migration, they misdiagnose the problem. Trust was already compromised—the migration simply made that reality unavoidable.
The First Trust Break
The moment business teams notice that numbers no longer match what they are used to, trust takes its first real hit. This moment is less about accuracy and more about surprise. Trust erodes not because the numbers changed—but because the change arrived without preparation.
This happens early in many cloud data migrations—and it is rarely handled with the seriousness it deserves.
“Why Doesn’t This Match With What We Had Before?”
The discrepancies are often small.
- A revenue total is off by a small percentage
- A customer count shifts slightly
- A report updates at a different time of day
From an engineering perspective, these differences are explainable:
- Cleaner joins
- Better deduplication
- Corrected historical logic
- Clearer cutoff times
From a business perspective, they often trigger alarm.
What business teams experience initially is not improvement—it is instability. The first reaction is rarely curiosity. It is fear:
- “Which number is right?”
- “Have we been wrong all this time?”
- “Which one will leadership use?”
Even when the new data is more correct, the change itself feels like a regression.
Precision vs. Familiarity
Familiarity reduces cognitive load. Precision increases it. Migration flips that balance overnight.Business teams do not instinctively trust newly accurate numbers.
They trust consistent numbers.
Legacy systems often produced results that were:
- Technically imperfect
- Internally inconsistent
- Operationally familiar
People learned the quirks:
- How rounding behaved
- When data “settled”
- Which filters to apply
- Which edge cases to ignore
Cloud migrations disrupt this familiarity.
Common sources of change include:
- Different rounding rules
- New data freshness windows
- Corrected time zone handling
- Explicit definitions replacing implicit ones
None of these are wrong. But they invalidate mental models business teams relied on to feel confident.
The result is a subtle but powerful shift:
“I used to know what this number meant. Now I’m not sure.”
Engineers Underestimate the Emotional Impact
For engineers, discrepancies are problems to diagnose.
For business teams, discrepancies feel like broken promises.
What they hear is:
- “The data is better now”
- “This is more correct”
- “The old system was flawed”
What they feel is:
- “The ground just shifted”
- “I might be embarrassed using this”
- “I don’t know which number is safe anymore”
This emotional gap is where trust fractures.
Engineers often respond by explaining logic in detail—joins, transformations, edge cases. But trust is not restored through explanations alone. Once business teams feel surprised by numbers, they become cautious.
They stop committing.
They double-check.
They delay decisions.
The first trust break in cloud data migration is not a bug or an outage.
It is the moment numbers change without a shared narrative explaining why the change is acceptable—and whether it is permanent.
Once this break happens, every subsequent discrepancy is interpreted through suspicion rather than curiosity. The first trust break is not technical. It is narrative. Numbers change before meaning is renegotiated—and trust pays the price.
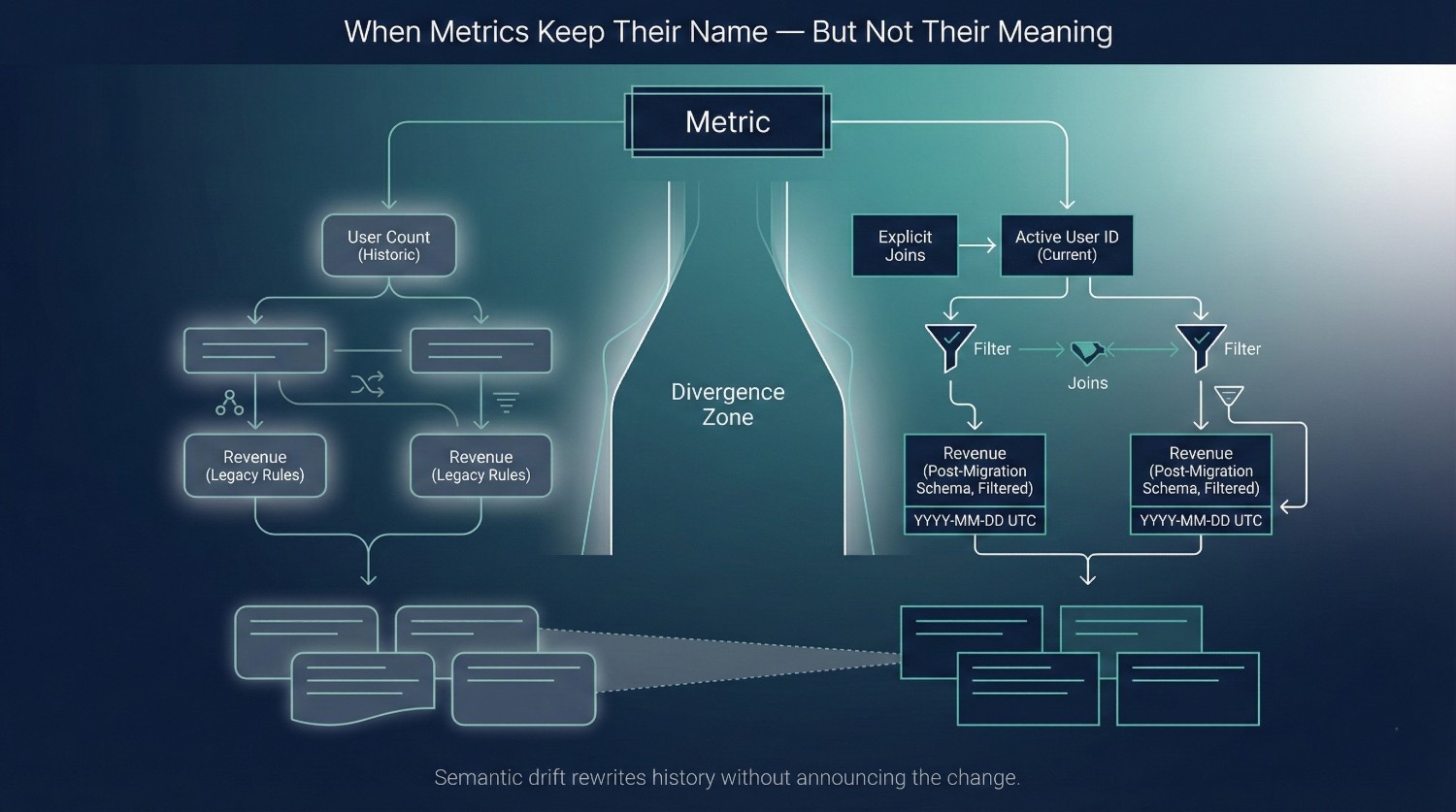
Semantic Drift
One of the most damaging trust failures in cloud data migration is semantic drift—when a familiar metric retains name, but quietly changes meaning.
No alert fires.
No one announces the change.
But the business feels it immediately.
“Revenue”
Before migration, “revenue” may have meant:
- Invoiced revenue, regardless of payment status
- Revenue excluding refunds until month-end
- Revenue aligned to booking date, not fulfillment
After migration, it may now mean:
- Recognized revenue only
- Net of refunds in real time
- Aligned to transaction completion timestamp
Both definitions are defensible.They are not operationally interchangeable.
Defensibility is not the issue. Continuity is. Business trust depends on knowing when a number is comparable to its past—and when it is not.
“Active User”
Previously:
- Logged in at least once in 30 days
- Excluding internal users by convention
- Counted from a single product system
After migration:
- Activity defined by events, not logins
- Internal users filtered explicitly
- Joined across multiple platforms
The number changes—not because usage changed, but because meaning did.This is why semantic drift is so hard to detect technically. Data quality checks pass, pipelines succeed, and dashboards refresh—yet confidence drops because the comparison frame has shifted.
“Conversion”
Before:
- Lead to opportunity created
- Measured when sales touched the record
- Dependent on CRM workflows
After:
- Lead to payment completed
- Event-based, time-bounded
- Aligned to product telemetry
The word stays the same.
The business implication does not.
Why Definitions Quietly Change During Migration
Most teams underestimate how many definitions were never truly defined. Migration forces implicit assumptions into code—and assumptions behave differently once they are explicit.
Semantic drift rarely comes from negligence. It emerges from structural changes that seem reasonable in isolation:
- Schema redesign
Fields are renamed, split, or normalized to improve clarity—changing how metrics are derived. - New joins
Additional tables introduce filters that were previously implicit or ignored. - New filters
Null handling, deduplication rules, or exclusion logic is formalized instead of assumed.
Each change improves technical correctness. Together, they redefine business meaning.
The Business Impact
This is where trust takes a deeper hit.
- Old reports no longer align with decisions
Teams cannot reconcile past outcomes with current numbers. - Historical narratives break
Trends no longer “make sense” because the underlying definition shifted mid-story.
Business leaders rarely experience this as improvement. They experience it as revisionism:
“If this number means something different now, what do our past decisions mean?”
At this point, skepticism replaces curiosity. Once skepticism sets in, even unchanged metrics are questioned. Trust loss spreads laterally, not just to the definitions that moved.
Semantic drift is not a technical bug.
It is primarily a communication and governance failure.
When metrics change meaning without being renamed, versioned, or clearly explained, cloud data migration breaks trust at a conceptual level. The business doesn’t just doubt the numbers—it doubts the continuity of its own history. Preventing semantic drift requires treating metric definitions as versioned assets, not implementation details. Without explicit versioning and ownership, migrations rewrite history without ever intending to.
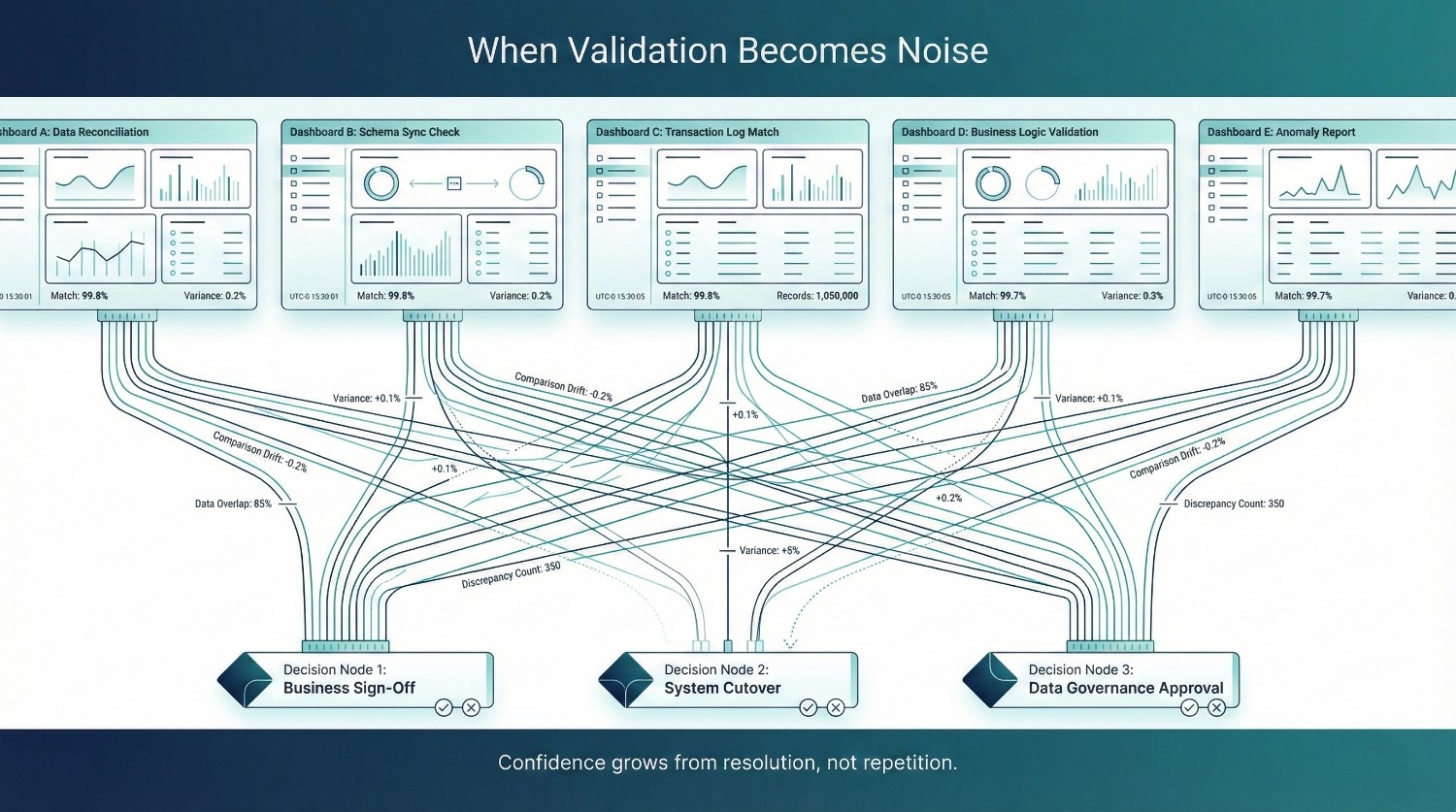
When Validation Becomes Noise
Validation is supposed to build trust.
In many cloud data migrations, it can do the opposite.
What starts as a responsible effort to reassure the business can slowly turn into a wall of conflicting signals that no one can interpret with confidence.
Too Many Dashboards
During migration, teams often create parallel dashboards:
- Legacy vs new
- Old logic vs revised logic
- Finance view vs product view vs operations view
Each dashboard answers a slightly different question. Each one is individually technically justified.
From the business perspective, this creates paralysis:
- “Which dashboard should I use for this meeting?”
- “Which one is the official number?”
- “Why do these three answers differ?”
Choice replaces clarity—and excess choice is not what business teams want from data. In practice, parallel dashboards shift responsibility from the system to the user. Instead of being told what to trust, business teams are asked to decide—without authority or context.
Too Many Comparisons
Comparisons are meant to narrow uncertainty. When they multiply without closure, they do the opposite: they expand the surface area of doubt.Side-by-side comparisons are useful early on. Left unmanaged , they become overwhelming.
Common patterns include:
- Daily variance reports no one can contextualize
- Percentage differences without explanation
- Long lists of edge cases labeled “expected discrepancies”
At some point, business users struggle to distinguish signal from noise. Every comparison looks like a potential problem—even when nothing is actually wrong.
Validation that cannot be interpreted becomes operationally indistinguishable from failure.
Too Many “Almost Matching” Numbers
Few things erode trust faster than numbers that are nearly the same.
- “It’s only off by 0.8%”
- “That difference is expected”
- “It should converge over time”
Engineers hear reassurance.
Business teams hear uncertainty.
If numbers are close but not equal, users don’t know whether to:
- Ignore the difference
- Explain it
- Defend it
- Escalate it
When this happens repeatedly, people stop engaging. The cost of asking questions feels higher than the value of the answer.
The Paradox: More Validation ≠ More Confidence
Confidence grows from resolution, not repetition. Validation that does not end in a clear outcome trains the organization to distrust its own processes.There is a tipping point where additional validation stops increasing trust and begins reducing it.
Past that point:
- Every discrepancy feels suspicious
- Every explanation feels provisional
- Every number feels negotiable
Instead of confidence, the business experiences fatigue.
When Business Teams Stop Listening
The final stage is often quiet disengagement.
Business teams:
- Stop reviewing validation reports
- Stop asking clarifying questions
- Stop trusting “this will be fixed later”
- Stop using the new platform for decisions
Not because they are resistant—but because validation has become noise rather than assurance.
Validation builds trust only when it leads to decisions:
- This difference matters
- This difference does not
- This definition wins
- This comparison is retired
Without those closures, cloud data migration overwhelms the business with information while withholding certainty.
And uncertainty, repeated often enough, sounds exactly like failure. Validation should reduce uncertainty over time. When it increases it, the migration has crossed from diligence into dysfunction.
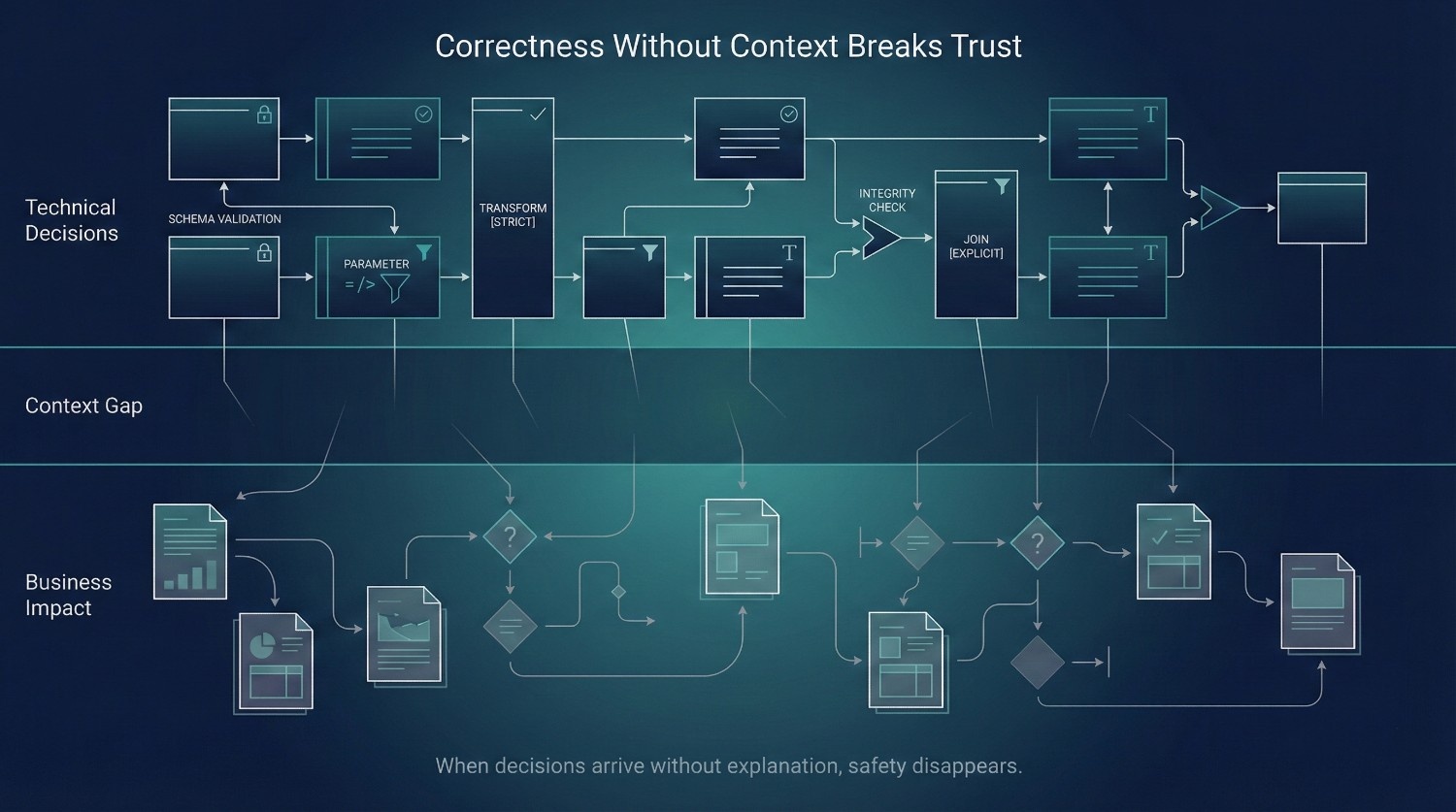
Lack of Business Context in Technical Decisions
One of the fastest ways cloud data migration breaks trust is when technically correct decisions are made without sufficient business context.
From an engineering standpoint, these choices are rational—even necessary.
From a business standpoint, they often feel abrupt, punitive, and unexplained.
Both sides are acting logically. They are optimizing for different outcomes.
This disconnect is rarely about competence. It is about incentive alignment. Engineers are rewarded for correctness and robustness; business teams are rewarded for continuity and confidence in decision-making.
Engineers Optimize for Correctness
Engineering decisions during migration tend to prioritize:
- Data integrity
- Logical consistency
- Clear constraints
- Reduced ambiguity
These are necessary goals for a data platform.
But correctness alone is not how business teams experience or evaluate data. Business teams experience data through consequence. A number is trusted not because it is provably correct, but because it behaves predictably when decisions depend on it.
Business Optimizes for Usability
Business teams optimize for:
- Continuity with past reports
- Predictable behavior over time
- Numbers they can explain confidently
- Outputs that support decisions, not debates
When usability is sacrificed abruptly—even in the name of correctness—trust drops.
No Shared Decision-Making Model
The core problem is not disagreement.
It is the absence of a shared model for deciding trade-offs.
Without one:
- Engineers decide what is “right”
- Business reacts to what feels “wrong”
- Neither side feels heard
- Trust erodes quietly
The migration becomes a series of surprises rather than a guided transition.
Examples of Technically Correct, Emotionally Damaging Decisions
These decisions often look small. Their impact is not.
Removing “Dirty” Rows
Engineers remove records with missing or invalid fields to improve data quality.
Business impact:
- Historical totals suddenly drop
- Past performance appears worse
- Teams feel like history was rewritten
Normalizing Categories
Free-text or loosely defined categories are standardized into enums.
Business impact:
- Familiar groupings disappear
- Long-used labels no longer exist
- Teams lose the ability to slice data the way they used to
Enforcing Stricter Constraints
Nulls, duplicates, and overrides are blocked or flagged.
Business impact:
- Edge cases stop appearing
- Exceptions require new processes
- Flexibility is replaced with friction
Each decision improves the technical system.
Each one also removes a coping mechanism the business relied on.These coping mechanisms were never ideal—but they were stabilizing. Removing them without replacement creates exposure before confidence is rebuilt.
Why This Breaks Trust
From the business perspective, these changes feel:
- Sudden
- Unilateral
- Hard to explain upward
- Risky to rely on in meetings
Trust does not break because the data is incorrect.
It breaks because people no longer feel safe using it.
Cloud data migration fails business teams when correctness is introduced without context, narrative, or meaningful choice.Choice matters because it restores agency. When the business participates in trade-offs, correctness feels collaborative rather than imposed.
Trust is preserved when technical improvements are:
- Explained before they land
- Framed in business terms
- Rolled out with clear intent
- Accompanied by ownership and decision-making support
Without that bridge, even the best engineering decisions quietly undermine confidence—the very thing the migration was meant to strengthen. The goal is not to slow down engineering decisions, but to sequence them—so improvements arrive with understanding, not surprise.
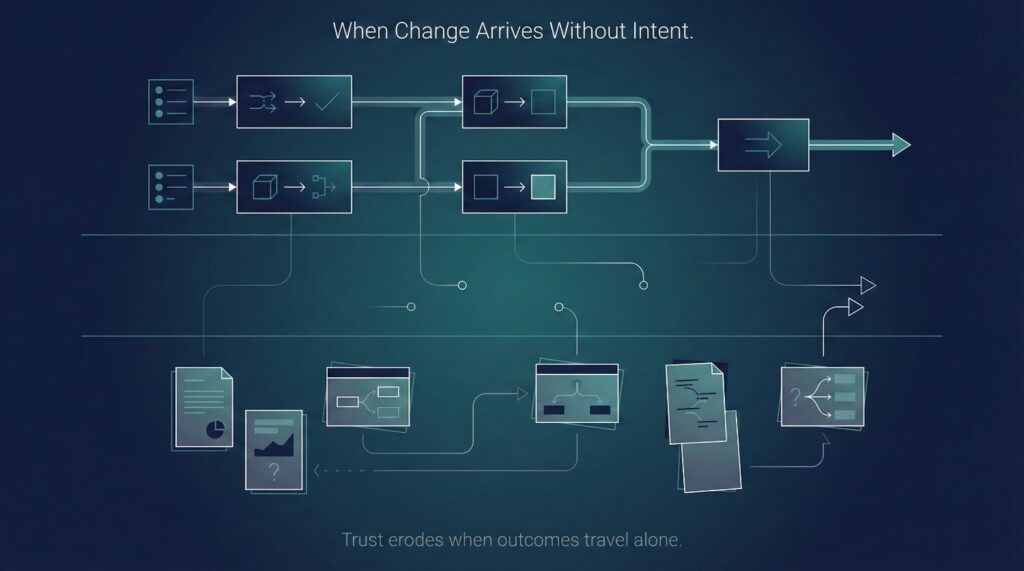
Communication Breakdown During Migration
Much trust loss during cloud data migration is not caused by what changes—it is caused by how those changes are communicated.
Or more accurately, how they are not.
When communication fails, even correct decisions can feel arbitrary, and even improvements feel unsafe. Communication failures turn technical change into perceived randomness. When outcomes arrive without intent, the business cannot distinguish deliberate progress from accidental disruption.
Business Hears Outcomes, Not Intent
In many migrations, business teams first learn about changes only after they have already landed.
What they hear:
- “This metric has been updated”
- “The numbers are more accurate now”
- “This report was fixed”
What they don’t hear:
- Why the change was necessary
- What trade-offs were considered
- What behavior is now expected
- Whether this change is final or provisional
Without communicated intent, outcomes feel imposed. Intent answers the unspoken question every business user has: “What am I supposed to do differently now?” Without that answer, caution replaces confidence.
Business teams are left to infer meaning on their own—and inference is where anxiety grows. Even positive changes feel risky when people don’t understand the reasoning behind them.
Language Mismatch
This mismatch is not about vocabulary—it is about responsibility. Engineers describe construction; business teams are accountable for consequences. Even when communication happens, it often misses its audience.
Engineers naturally explain work in terms of:
- Pipelines
- Joins
- Backfills
- Schema changes
- Validation logic
Business teams think in terms of:
- Can I trust this number?
- Will this change again?
- Can I defend this in a meeting?
- Does this affect my targets?
When engineers communicate how something was built instead of what it means, reassurance is lost. The explanation may be technically accurate—and completely ineffective.
Trust requires translation, not technical detail.
Why Slack Updates Aren’t Communication
Activity updates create the illusion of transparency. But transparency without interpretation still leaves the business guessing. Many migrations rely on frequent Slack updates as a proxy for transparency.
The problem is not frequency. It is framing.
Typical updates look like:
- “Backfill complete”
- “Validation ongoing”
- “Minor discrepancies expected”
- “Fix deployed”
These updates share activity, not narrative.
What’s missing:
- What changed from the business point of view
- Whether users need to adjust behavior
- Whether numbers are now stable
- Whether something is safe to rely on
Without narrative:
- Updates are skimmed
- Reassurance is absent
- Silence is interpreted as uncertainty
Business teams don’t disengage because they weren’t informed.
They disengage because they were never guided toward safe usage
Effective communication during cloud data migration is not about more messages.
It is about intentional framing:
- What changed
- Why it changed
- What it means for decisions
- Whether it will change again
When migrations fail to provide that framing, trust erodes—even when the underlying work is sound.
The next section will show how this communication gap becomes permanent when no one is clearly accountable for answering business questions with authority. Sound engineering cannot compensate for silent leadership. Trust depends less on what changed than on whether someone stands behind it with clarity.
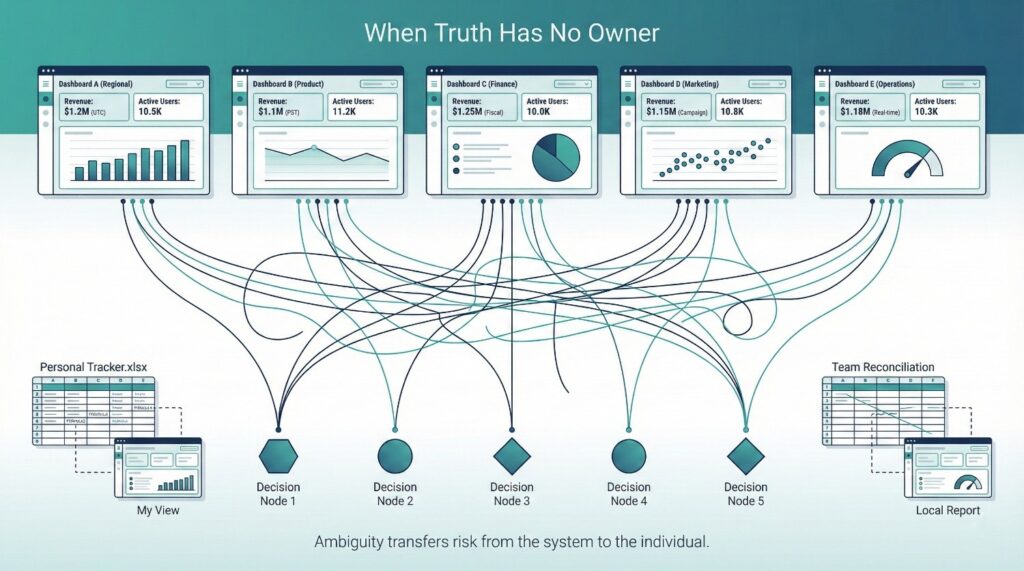
No Clear Owner of “Truth”
Trust collapses fastest when business teams cannot answer a basic question:
“Who decides what the correct number is?”
In many cloud data migrations, there is no clear answer. When ownership is unclear, correctness becomes theoretical. A number can be technically sound and still unusable if no one is empowered to stand behind it.
Multiple Dashboards, No Authority
As migrations progress, it is common to see:
- Multiple dashboards answering the same question
- Slightly different numbers across tools
- Teams publishing their own “working versions”
Each dashboard is defensible in isolation. Together, they signal disorder.
When no dashboard is explicitly authoritative, business users are forced to choose—and choice without guidance increases perceived risk. Forced choice transfers risk from the system to the individual. Business users are left personally accountable for picking the “wrong” number.
Conflicting Definitions, No Resolution
Metrics diverge because:
- Teams apply different filters
- Time windows differ
- Edge cases are handled inconsistently
- Definitions evolved during migration but were never locked
The real issue is not disagreement itself.
It is that disagreements never resolve.
Without a defined owner:
- Questions bounce between teams
- Engineers explain logic but cannot decide
- Analysts provide context but lack authority
- Meetings end without closure
The same debates resurface week after week.
No Escalation Path
Escalation is not about hierarchy—it is about finality. Someone must be able to say “this is the answer we are using,” even when it is imperfect.When conflicts arise, business teams look for escalation:
- Who can settle this?
- Who can say “this definition wins”?
- Who can take responsibility if it’s imperfect?
In many migrations, there is no clearly defined escalation path. Decisions stall because no one is empowered to make them.
Silence replaces clarity.
The Business Response: Self-Protection
Business teams adapt rationally to this ambiguity.
When truth is ambiguous, they reduce personal risk:
- “I’ll trust my own numbers”
- “This is just for internal use”
- “Let’s sanity-check it in Excel”
This is not defiance.
It is self-preservation.
Shadow Analytics Emerges
Once trust breaks, shadow systems appear:
- Private spreadsheets
- Team-specific dashboards
- Manual reconciliations before meetings
These systems feel safer because they are controlled—even if they are less accurate.
At that point, the cloud data migration has lost its purpose. The platform exists, but authority does not.
Cloud data migration breaks trust when truth has no clear owner.
Business teams do not expect perfection.
They expect clarity about:
- Which number is official
- Who owns it
- How disagreements are resolved
Without that, the only safe option is to stop trusting shared data altogether—and build their own truth instead. Naming an owner does not eliminate disagreement. It ensures disagreement ends in a decision—and decisions are what trust needs to form.
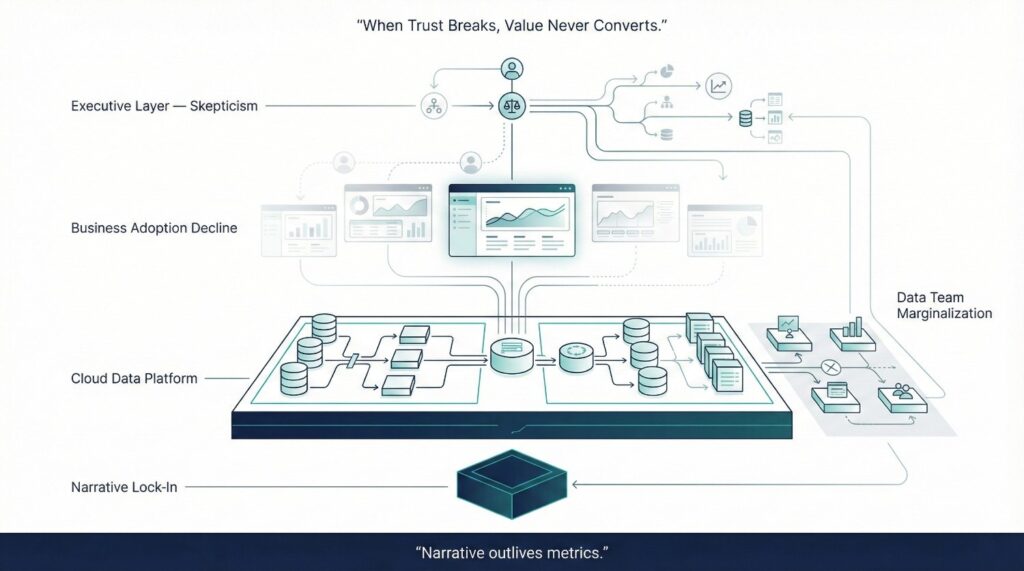
The Cost of Broken Trust
When trust breaks during cloud data migration, the impact is rarely immediate or dramatic. It accumulates quietly—and then becomes very hard to reverse.
The platform may be live.
The data may be correct.
The engineering work may be sound.
None of that matters if the business no longer has confidence in it. Confidence is the conversion layer of a data platform. Without it, technical capability never translates into operational value.
Reduced Adoption
Adoption is the earliest measurable signal of trust loss. Usage declines before complaints surface—and long before leaders are willing to call the migration a problem.The first visible cost is low usage.
Business teams:
- Stop using dashboards for decisions
- Treat reports as “directional only”
- Export data to spreadsheets before acting
- Ask for one-off confirmations “just to be safe”
Adoption drops not because the platform is slow or broken—but because relying on it feels personally risky.
Without adoption, the migration delivers no real value.
Executive Skepticism
Executives sense hesitation before they see metrics.
When numbers are:
- Qualified instead of asserted
- Explained defensively
- Prefaced with “this might change”
Confidence erodes at the top.
Leadership begins to question:
- Whether the migration was worth the cost
- Whether the data team understands the business
- Whether future initiatives should be trusted
Once executive skepticism sets in, recovery becomes organizational and political—not technical.
Data Teams Sidelined
When trust is low, data teams lose influence.
Their outputs are:
- Second-guessed
- Cross-checked manually
- Used only after validation by someone else
Over time, data teams are pulled out of strategic conversations and repositioned as report producers rather than decision partners.
This is one of the most damaging outcomes of a failed trust transition during migration.
Migration Labeled a Failure—Even If Technically Sound
Eventually, the narrative solidifies:
“The migration didn’t really work.”
This label often sticks regardless of technical reality.
The platform may be faster.
Costs may be lower.
Reliability may be higher.
But because trust was lost, the migration is remembered as a failure. Narrative outlives metrics. How a migration is remembered matters more than how it performed on paper.
Future efforts inherit that baggage:
- Increased resistance
- Longer approval cycles
- Lower tolerance for change
Broken trust is not a “soft” problem.
It is an outcome that directly undermines ROI, credibility, and momentum.
Cloud data migration fails in the business not when systems break—but when belief breaks.
How Trust Actually Gets Rebuilt
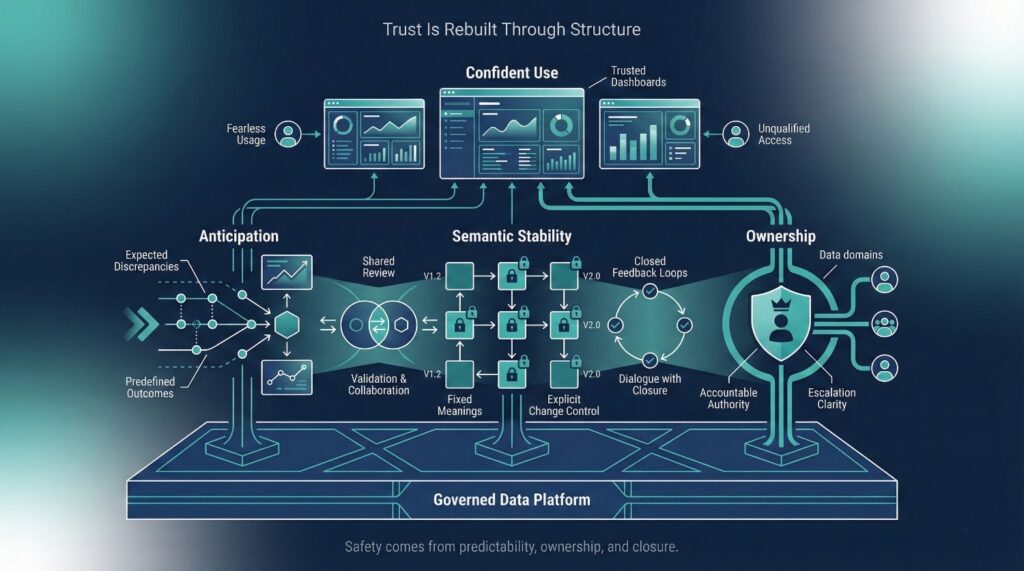
Once trust is damaged, it rarely comes back through better queries or faster dashboards alone. It comes back when the business feels safe relying on the data again.Safety is rebuilt when behavior becomes predictable. Trust returns not because data is perfect, but because teams know what will happen when they use it—and who will stand behind the result.
That safety must be created deliberately. Not through reassurance—but through structure, predictability, and shared ownership.
Make Discrepancies Expected, Not Surprising
One of the fastest ways to lose trust is to let business teams discover differences on their own.
Instead:
- Pre-announce expected differences
Tell stakeholders before rollout which numbers will change, by how much (roughly), and in which reports. - Explain why they exist in business terms
Not joins or backfills—explain the reason in terms of policy, timing, or definition changes that affect decisions.
When discrepancies are expected, they are processed calmly.
When they are surprising, they trigger fear.
The difference is not accuracy. It is anticipation.
Anticipation shifts control back to the business. It allows leaders to prepare explanations instead of reacting defensively.
Freeze Semantics Before Optimizing
Semantic stability is the foundation of confidence. Optimization without stability feels like constant renegotiation of meaning.Trust cannot survive on constantly shifting ground.
Before performance tuning, cost optimization, or refactoring:
- Lock metric definitions
Decide what “revenue,” “active,” or “conversion” means now—and commit to it. - Version changes explicitly
If a definition must change later, rename it, version it, or announce it as a deliberate shift—not a silent improvement.
Business teams can adapt to slower or less elegant systems.
They cannot adapt to meaning that keeps changing.
Stability of semantics matters more than technical elegance.
Put Business in Validation Loops
Validation should not be something the business is asked to approve only at the end.
Trust grows when validation is collaborative:
- Invite business users into discrepancy review
Ask which differences matter for decisions and which do not. - Treat validation as dialogue, not sign-off
The goal is shared understanding, not formal approval. - Close the loop explicitly
When a discrepancy is accepted, say so—and stop revisiting it.
This shifts validation from “prove you’re right” to “decide together what’s acceptable.”
That shift alone restores a surprising amount of confidence.
Ownership converts ambiguity into authority. It signals that someone is accountable for decisions—even when trade-offs are imperfect.Trust requires visible authority.
Business teams need to know:
- Which dashboard is official
- Which definition applies
- Who owns it
- How disagreements are resolved
That means:
- Naming a clear owner for each critical metric
Not a team—an accountable role. - Publishing escalation paths
When numbers conflict, people should know exactly where to go. - Making ownership visible, not implied
Ownership should be written down, not inferred through meetings.
When truth has an owner, trust becomes possible—even if the numbers are imperfect.
Trust is rebuilt when cloud data migration stops feeling like a moving target and starts feeling like a governed system.
Business teams do not need perfection.
They need predictability, clarity, and a sense that someone is standing behind the numbers.
When those conditions are met, confidence returns—not all at once, but steadily enough for the migration to finally deliver the value it promised.
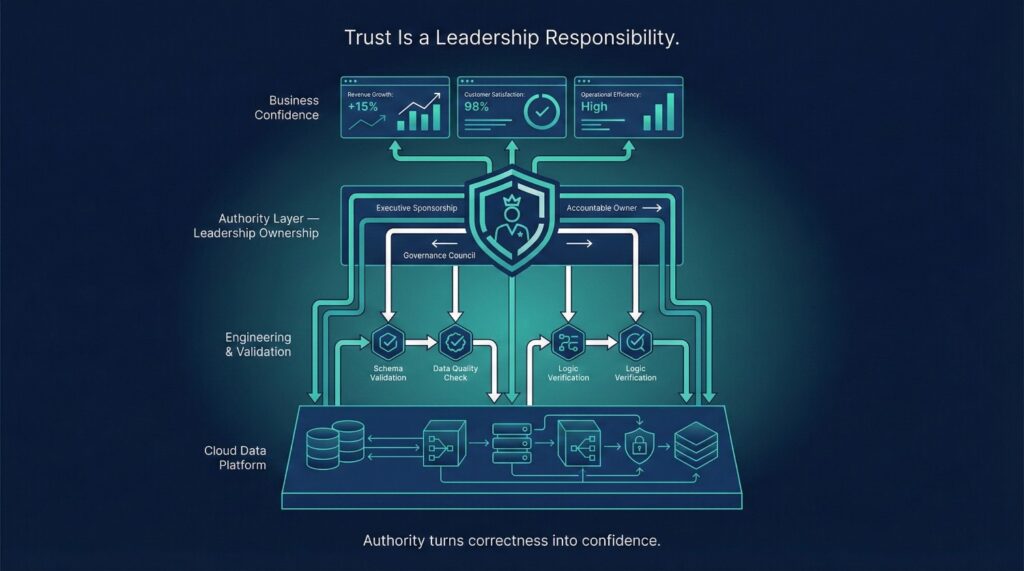
Why Trust Is a Leadership Responsibility
Trust does not fail because engineers lack skill alone.
It fails because no one with authority is visibly responsible for protecting it.
Cloud data migration puts pressure on meaning, history, and decision-making. Those pressures cannot be resolved at the implementation layer alone.
Trust Cannot Be Delegated to Engineers
Delegation works for execution, not for legitimacy. Trust requires someone whose authority extends beyond correctness into consequence.
Engineers can:
- Build correct pipelines
- Validate data rigorously
- Explain discrepancies clearly
They cannot:
- Decide which definition wins when metrics conflict
- Absorb the political cost of changing numbers
- Reassure the business that a number is safe to use
- Commit the organization to a source of truth
When trust-related decisions are pushed down to engineers, three things happen:
- Decisions stall because authority is missing
- Engineers over-explain instead of deciding
- The business hears uncertainty instead of confidence
Trust erodes—not due to mistakes, but due to hesitation. Hesitation signals uncertainty at the top. When leaders hesitate, the business assumes the numbers are provisional—even when they are not.
What Trust Actually Requires
Rebuilding and maintaining trust during cloud data migration requires leadership actions that cannot be automated or outsourced.
Executive Backing
Leadership must publicly stand behind the migration and its outputs:
- Acknowledge that numbers may change
- Frame changes as intentional, not accidental
- Defend the platform when questions arise
Without this backing, every discrepancy feels like a failure rather than a step forward.
Decision Authority
Someone at the leadership level must be empowered to decide:
- Which metric definition is official
- When validation is sufficient
- When cutover happens
- When legacy reports are retired
Trust collapses when decisions are endlessly deferred in the name of alignment.
Visible Accountability
Business teams need to see that:
- Someone owns the truth
- Someone is answerable when numbers are questioned
- Someone will make a call even when certainty is incomplete
Accountability restores confidence because it removes ambiguity about who stands behind the data.
Trust in cloud data migration is not built by flawless execution alone.
It is built when leadership chooses clarity over comfort and visibly owns the consequences of that choice.
When leadership treats trust as its responsibility—not an engineering side effect—business teams stop protecting themselves and start relying on the platform again.
And that is when a migration finally becomes “successful” in the only sense that matters.
The Counterintuitive Truth
It feels backward, but it is consistently true:
Business trust improves when uncertainty is acknowledged and actively managed—not hidden.
Cloud data migration makes this unavoidable. It removes the ability to quietly smooth over problems, forcing organizations to confront reality in the open.
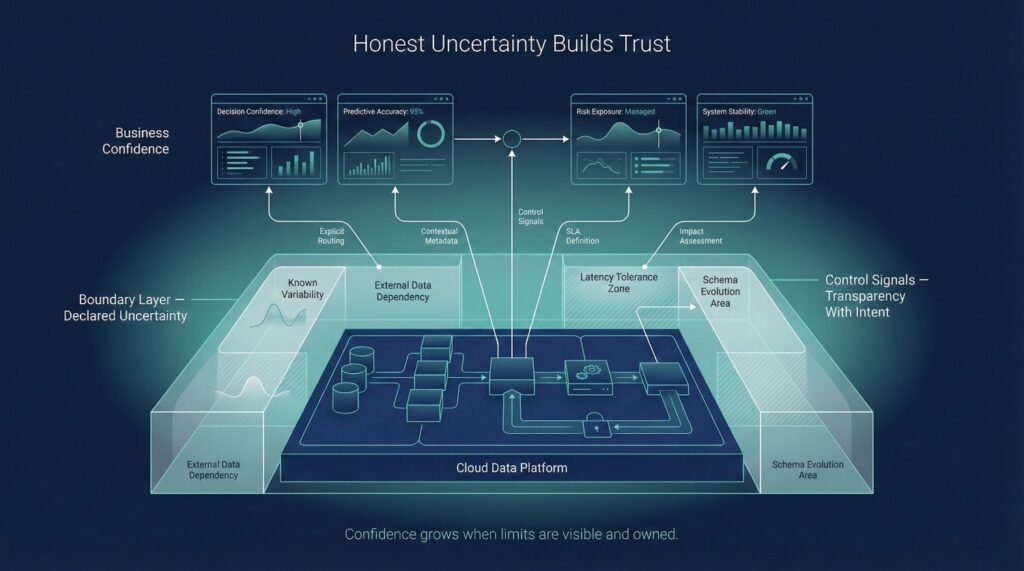
Honest Uncertainty Builds Confidence
Business teams do not expect perfect data.
They expect predictable behavior and honest communication.
Trust increases when leaders say things like:
- “This number may shift slightly while definitions are finalized.”
- “These two reports differ for a known reason, and here’s which one to use.”
- “We’re choosing this definition because it supports better decisions—even though it changes historical comparisons.”
These statements don’t weaken confidence. They strengthen it—because they signal control, not confusion.
When uncertainty is acknowledged upfront, it stops feeling like a threat. Acknowledgment reframes uncertainty as a known variable, not an unknown danger. Once named, it becomes something the business can plan around instead of fear.
Controlled Transparency Beats False Certainty
False certainty creates short-term comfort and long-term damage.
When organizations:
- Present numbers without caveats
- Hide discrepancies to avoid questions
- Treat uncertainty as something to conceal
they borrow trust they cannot repay later.
Controlled transparency works differently:
- Differences are surfaced deliberately
- Context is provided before people discover issues themselves
- Limits and trade-offs are explained in business terms
This does not make the data feel risky.
It makes it feel managed.
Business teams trust systems more when they understand their boundaries than when those boundaries are hidden.
Cloud Migration Forces Honesty
Legacy systems allow ambiguity to persist quietly:
- Manual fixes patch over inconsistencies
- Reconciliations happen out of sight
- Assumptions remain unspoken
Cloud data migration removes many of those escape hatches.
It forces organizations to:
- Make definitions explicit
- Surface inconsistencies early
- Explain why numbers behave the way they do
- Own decisions rather than imply them
This can feel destabilizing at first. But it creates a stronger foundation.
When risk is visible:
- It can be discussed without panic
- It can be assigned ownership
- It can be reduced intentionally
The counterintuitive lesson of cloud data migration is this:
Trust does not come from pretending everything is stable. It comes from showing that instability is understood, bounded, and actively managed.
Business teams rely on confidence—not perfection.And confidence grows fastest when honesty replaces illusion.
In mature organizations, honesty becomes a stabilizing force. When uncertainty is bounded and owned, confidence compounds instead of eroding.
Final Thoughts
Cloud data migration does not break trust by itself.
Silence often does.
Trust erodes not when numbers change, but when changes arrive without explanation or framing.
Not when definitions evolve, but when decisions are made invisibly.
Not when systems improve, but when the business feels left out of the process.
When Trust Fails
These failure modes are predictable because they follow human behavior, not system behavior. When people lack context and ownership, they default to caution. Trust fails predictably when:
- Changes are unexplained
Numbers shift without warning, context, or narrative, leaving business teams to guess whether they are safe to use. - Decisions are hidden
Definitions change, edge cases are handled, and trade-offs are made without clear ownership or visibility. - The business feels excluded
Validation happens in isolation, communication is one-way, and feedback loops close without shared understanding.
In these conditions, even technically correct data can feel unreliable. Reliability is experiential, not theoretical. A system can be correct and still be unusable if people do not feel safe standing behind its outputs.
When Cloud Migrations Succeed
Cloud data migration succeeds with the business when trust is treated as an explicit outcome – not an accidental byproduct.
That happens when:
- Trust is treated as a deliberate deliverable
Just like performance or cost, trust is planned for, protected, and measured through adoption and confidence. - Communication is intentional and proactive
Changes are framed before they land, explained in business terms, and reinforced until they feel stable. - Leadership stays engaged
Executives visibly own decisions, stand behind definitions, and provide clarity when uncertainty arises.
When these conditions are met, migration stops feeling disruptive and starts feeling directional to the business.
Cloud data migration does not fail simply because the platform is new.
It fails when people are left to interpret change alone. Interpretation without guidance creates fragmentation. Each team constructs its own version of truth—and shared confidence disappears.
When leadership replaces silence with clarity—and surprise with intent—trust does not merely survive migration.It can become stronger than it ever was before.
The ultimate measure of migration success is not system performance, but organizational reliance. When leaders replace silence with clarity, the platform becomes something the business trusts—not just something it uses.
Frequently Asked Questions (FAQ)
Not by itself. Trust breaks when changes happen without explanation, ownership, or context. Migration exposes differences and forces decisions; silence and surprise, not the technology, are what undermine confidence.
Because they don’t feel safe relying on it. When numbers change unexpectedly, definitions shift quietly, or no one can clearly say which dashboard is authoritative, business users protect themselves by reverting to spreadsheets or shadow reports.
Because they create social risk. Business users worry about being challenged in meetings, missing targets, or explaining numbers that may change again. A 1% difference can feel bigger than a system outage if it undermines confidence.
Semantic drift happens when a metric keeps the same name but changes meaning during migration. This breaks historical continuity. Leaders can no longer reconcile past decisions with current numbers, which erodes trust at a conceptual level.
Only up to a point. Too many dashboards, comparisons, and “almost matching” numbers create noise. When validation doesn’t lead to decisions—what matters, what doesn’t, and what’s final—business teams stop engaging.
Because trust is not restored through technical explanations alone. Engineers can explain how numbers changed, but leadership must explain why those changes are acceptable and permanent. Without authority behind the explanation, uncertainty remains.
An explicitly named owner with decision authority—not a committee. Business teams need to know which definition is official, who stands behind it, and how conflicts are resolved.
By making discrepancies expected, freezing definitions before optimizing, involving business users in validation decisions, and publishing clear ownership. Trust returns when behavior becomes predictable and accountability is visible.
Yes. Trust cannot be delegated to engineers. It requires executive backing, decision authority, and visible accountability—especially when numbers change or trade-offs must be accepted.
Assuming silence equals stability. When leaders avoid uncomfortable conversations, business teams fill the gap with skepticism and self-protection. Clear, early communication is safer than delayed certainty.